I am back for part 2 of the analysis breakdown of the ICIT APT briefing. After an excellent discussion on the topic of Malware Evolution with someone from the Malware Bytes team, I think it is time to finish what I started several weeks ago. Here is the second half of my analysis or the APT report.
Sunday, April 24, 2016
Tuesday, April 19, 2016
The Jolly Roger Flies Again: BSides Tampa
This past Saturday I had the pleasure of presenting my Rellik Project once again. This time at the Security Bsides event in Tampa FL. Hosted by the (ISC)2. The topic of Botnets has been very popular and my audience was very involved. It was a fantastic day all around.
Sunday, April 10, 2016
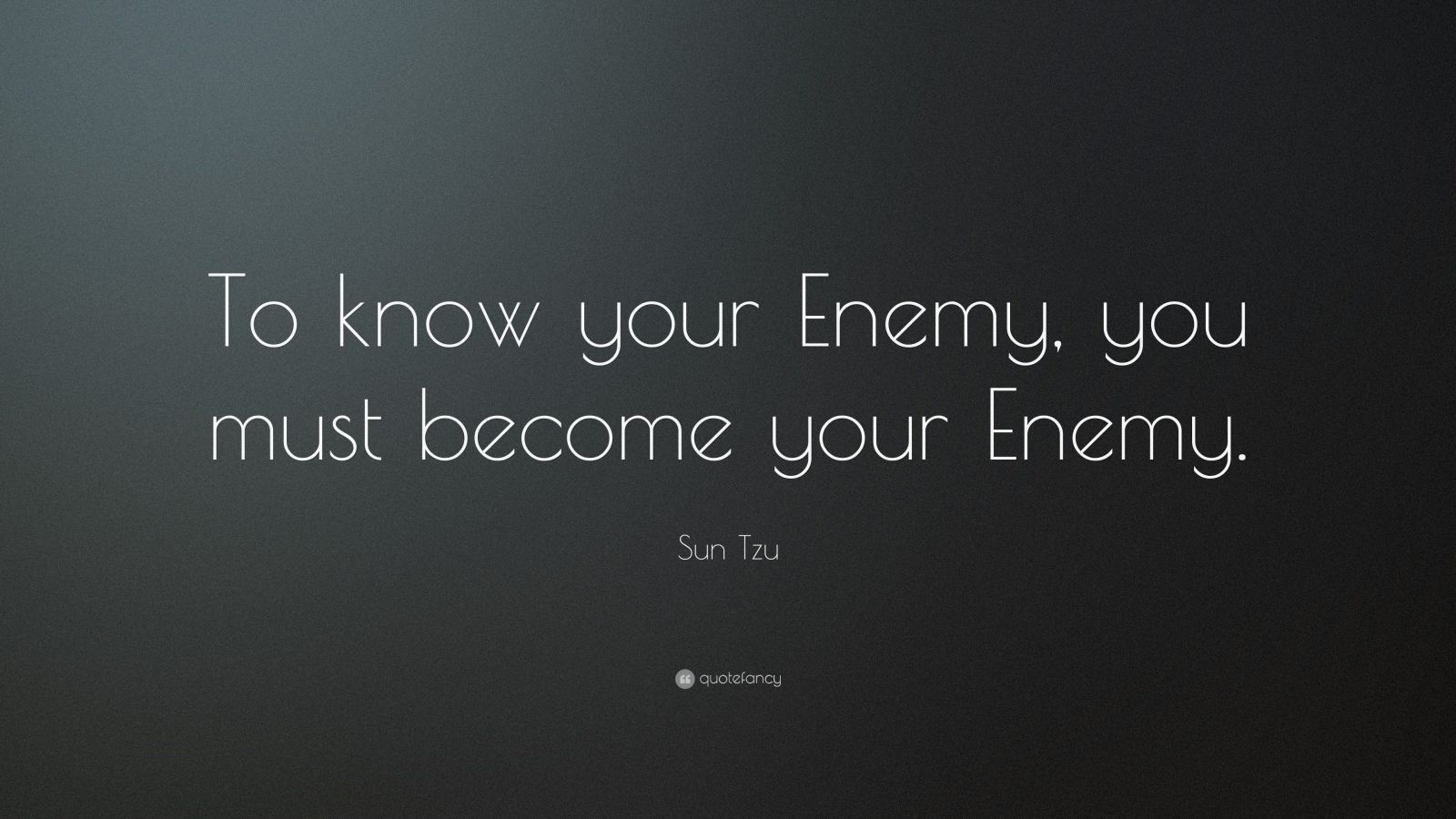
Knowing the Enemy: Advanced Persistent Threat report analysis Pt. 1
Advanced
Persistent Threats or APTs has become a well known term over the last 5 years. In terms on
Network security an attack is considered
Tuesday, April 5, 2016
Be careful what you wish for: Information Leaks in Job Searches
Your company is leaking data. That is not a question. It simply is a fact. The reason is: job postings. The amount of information companies give out freely about their organization, network technology, infrastructure, etc., is amazing. It is also a potential gold mine for a would be attacker. Consider the real (but edited for privacy) job description found on a very popular classified site:
Subscribe to:
Posts (Atom)