The importance of Katas
In certain Martial
Arts traditions there exists training forms known as Katas. They are
a detailed set of choreographed actions that you perform repeatedly.
One of the purposes of performing these scripted movements, is to
train your body to react seamlessly in common patterns. Of course,
you need to be able to improvise. But enough cannot be said about the
importance of drilling on the basics (and not so basics). As my instructor puts it "Flash may impress spectators, but fundamentals win fights"
These Katas
are designed with a particular scenario in mind and are often
performed by ones self. Part of the exercise is to imagine the
movements of your imagined opponent. Skilled Martial Artists can
study the movements of a Kata and “read” what the opponent would
be doing in each step as well. In this way it is a bit like deducing
both sides of a telephone conversation from only hearing one side.
The same idea can be applied to practicing common attack patterns for
Red Teams as well. To show how one might use this idea in practice I
will be using both Metasploitable3 (M3) and Metasploitable2 (M2).
Below are some ideas on attack patterns to practice. The grizzly
details of the exact commands will be left out for the most part
since these are highly dependent on your style.
Kata x00 – Enumerate the target area
Even if you only
have one machine and you know exactly every port and service running.
Enumerate it again. And Again. Enumerate your target VMs with 4-5 of your
favorite Nmap Scans working from quickest/Least info to slower/more
comprehensive. If you want to add a little more realism to this
training you can use python + vagrant provisions to randomly start or
stop certain services on the target VM.
 |
| Scanning Katas follow the principle of 'know thy enemy and know thy self' |
Kata x10 – Weak creds to DB User Access
This is a simple
Kata that should be familiar to anyone with Red Team Experience.
First setup a M2 VM (This is the Linux VM version) and your Attacker
machine. Now on the attack machine start a credential scan using the
top default user name and service passwords (unhashed). Once a set of
credentials is recovered (postgres:postgres for example) use an
exploit to get a command shell (reverse or not is up to you, but I
prefer reverse). As with Kata 0 you can add more realism by adding a
vagrant provision which randomly selects a new postgres password from
a set of passwords. I like to use the top 100k password list to
select the password from, then I use a smaller subset (top 10k or so)
list to start my cred scan. Good password lists to practice can be
found at
https://github.com/danielmiessler/SecLists/tree/master/Passwords
Kata x1a – Unless
you get extremely lucky the database will not be run as root, so this
extends the Kata x10 exercise to include a local privilege escalation
and instead return a root shell
Kata x1b – Extend
the Kata x10 exercise to exfiltrate the contents of the Database
Kata x20 – SQLi to Web Admin
Another simple Kata
that we see all over the place. Fire up M2 (or 3 if you prefer), and
start a Vulnerable Web App. Inject an admin user which gives you full
access to the chosen application. The exact method differs slightly
based on the table structure of the vulnerable web app you choose to
train against, so you may want to switch it up occasionally.
Kata x2a – Extend
Kata x20 by using the web admin access to get the Web Server user’s
level access to the system by uploading a Web Shell.
Kata x2b – Extend
Kata x2a by using the Web User’s access and a local privilege
escalation to get a root shell
Kata x30 – Exploit Network Service for Access
This is probably the
Kata most people think of when they think of hacking into a box. Some
vulnerable application is up and accepting traffic from the network.
I switch up which services I train against based off of what I want
to get out of my training session. Some popular choices are
- IRC
- FTP
- Java applications
 |
| It is important to remember the details. Check the options during your Katas |
As I mentioned in
Kata 0, I will use M2 or M3 plus vagrant provisioners to start
different combinations of services during different practice sessions
Kata x3a – Extend
Kata x30 by using a local privilege escalation to return a root
shell. This may not be required if the service you exploit was run as
root.
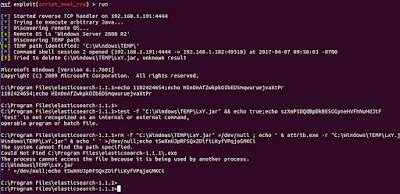 |
| Exploiting a Network Service. Is there anything more hackeresque? |
Kata x40 – Post Exploitation
This Kata extends
x1*, x2*, and x3* by adding in post-exploitation steps. This again comes down to your personal preference but there are some fundamentals that should not be overlooked even if they are not part of your normal routine. First and foremost create a reliable persistence method! Then run through commands to determine pertinent facts about the compromised system.
Kata x4a - Gather
running processes, logged on users, shares, known hosts, etc.
Kata x4b - Get list
of interfaces
Kata x4c - Install
Trusted Path Persistence
Kata x4d - Add Admin
level User
 | ||
| Add a user that will blend in with the other user names |
Kata x50 - Pivot to an internal network
This takes a bit
more setup of the VM environment. First you need to install
VirtualBox inside the guest. You will need to add a copy of the M2 VM
to the newly installed VirtualBox manager (inside M3). I will call
this VM M2b. Set the network setting to a host-only adapter. Once it
is set, start the M2b VM. Now there exists a machine that you can
only reach by pivoting through the M3 VM. This is analogous to
accessing a development machine that is behind a VPN gateway or on a
separate subnet.
I think the best way
to view this is as several separate Katas, linked together with some
special moves in the middle. First you enumerate the M3 VM (Kata
x00). Then you perform Kata x3a which leaves you with a root shell on
the first target. Next you perform Kata x4b which reveals the second
network interface and IP, Now for the special moves that make this
it’s own Kata: Use the root shell access and the information
gathered to setup a pivot point on the M3 VM. Using this pivot, start
back at the scanning Kata x00, but this time enumerate the M2b VM.
Finally, use Kata x2b to get root access on M2b.
Conclusion
These Katas
encapsulate all the fundamental skills required for a successful
digital Martial Artist to hone their skills. Sure there are other
necessary skills, not touched on (such as exploit development and
modification, scripting, etc.). Much the same way that every move is
not included in traditional Martial Arts Katas. Instead you should
train on those skills individually and in a more focused manner. Finally, do not be afraid to create your own Kata variations. the key is to practice them consistently and fluidly. Focus the design of each on applying your strengths against your opponent's weaknesses.

No comments:
Post a Comment